On the safety design of smart grid
For the smart grid, because the probability of attacking the grid infrastructure is increasing, the stable power supply of various countries is in danger of being maliciously attacked, thereby increasing the importance of security issues. In this regard, IT security is particularly important; many solutions support end-to-end communication data encryption, such as: data concentrators, monitors, and data collector systems (SCADA). The focus on IT encryption measures is unquestionable because of the need to ensure the security of data transmitted "over the air". However, even strong end-to-end encryption cannot protect the entire smart grid: the embedded device itself is vulnerable.
Is encryption equal to security?
Although encryption tools are very effective for privacy protection and authentication of transmitted data and commands, it must be noted that this is only part of the solution. The role of encryption is to prevent the protected data from being decrypted or forged during transmission or storage. Some people think that complex RF or power carrier communications rely on frequency modulation to fully guarantee data security. In fact, this type of protection is easily broken. Assuming that the attacker can arbitrarily control the remote meter closing relay, the power company will need to invest a lot of resources to deal with the fault. Power companies not only suffer economic losses, but also cause great troubles, posing a threat to the survival of those places where air conditioning must be used.
So, how to avoid such accidents? If both parties to the communication use the key to encrypt, decrypt, sign or verify the data on the communication line, data encryption from the embedded sensor to the control system is critical, and the key protection used for encryption is also more important. Once the key is stolen, the entire network is no longer secure. The embedded terminal of the smart grid needs a more complete security solution, which can draw on the security technology of the financial terminal, focusing on key protection, using chip-level hardware and multiple protection measures against attacks.
The protection of the power supply cannot be limited to the verification of valid data and commands of the smart grid. Worm makers understand the effective means of attacking embedded infrastructure, which is not easy to be discovered and causes serious damage to the system. The well-known "zero-day attack" uses the method of wiping out or modifying system programs, and the damage caused by the system is very hidden. Therefore, we should not only pay attention to the installation of the equipment, but also pay attention to any programming link (such as the production process) that is vulnerable to attacks.
What are the loopholes?
Achieving a safe and reliable design is not easy. It takes a lot of time and an in-depth understanding of security protection technology. So, are these investments worth it? Let's first analyze a smart meter connected to the Internet. For example, an meter installed in our own home without protection measures can be easily opened by outsiders. If the meter uses a general-purpose MCU to handle communication and application functions, there is likely to be a programming port where an attacker can reprogram him or read internal information. Under the premise of sufficient resources and time, some people can write a program with similar functions, but implant a virus that obtains key data or tampers with the bill in the program.
Even the electric meters connected to the network have certain protective measures to prevent tampering to a certain extent. We can still find some links that are vulnerable to attack-the production link. The so-called "social engineering" provides an opportunity for attackers to invade IP and production processes. At a cost of thousands of dollars, an attacker may obtain a program, modify it through reverse engineering, and implant a "new program" into the product. In addition, an attacker can also sell your program to competitors, causing huge losses.
How to ensure the safety of equipment life cycle?
The strict product production process should consider the security of every link from design to production, as well as strategies to deal with tampering. To ensure the safety of the life cycle, the following points need to be considered:
1. Make sure that the chip you obtained is produced from the original factory and purchase through regular channels to reduce risks. Of course, encryption technology must also be considered. Maxim's security processors and smart grid products can add user keys or certificates to prevent others from unlocking and programming the IC.
2. Protect your IP. Provide signatures and program encryption in the factory production link, and coordinate every link from the secure loading of the system processor to chip software decryption and authorization certification. This type of encryption prevents the program from being cloned or cracked.
3. Only run the program you specified. Secure program loading uses digital signatures to verify the validity of the code to prevent loading or running unauthorized code.
4. Reliable communication. Encrypt and sign new configurations, firmware updates, and instructions to verify the reliability of data sources.
5. On-site protection key. Do not store the key elsewhere, such as external EEPROM. If the system uses independent security processors and application processors, the key should be stored in the security processor and not sent out. In order to prevent the attacker from stealing the key from the communication data of the circuit board.
6. Key protection within the company. Engineers can use development keys to develop product security features, and product-level keys are subject to multi-signature authorization. Usually a higher level security module can be used for authorization.
7. Don't miss every tiny loophole. If the system attacker only steals important information from a meter, and invests a lot of time and money to study this information, hoping to attack the entire system accordingly. Experienced attackers may open the IC package and look for important information in the MCU's memory. Therefore, it is necessary to use a unique key or asymmetric encryption (such as elliptic curve digital signature).
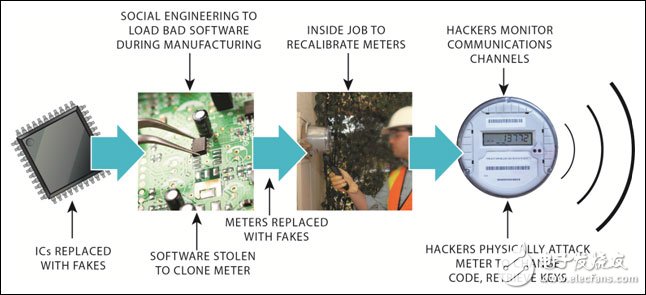
Figure 1. Security in the product life cycle needs to consider every detail from development to production.
The current security measures of the power grid leave a lot of room for attackers. In order to ensure the safety of embedded devices throughout the entire life cycle, we also need to strengthen the security design of the entire smart grid to prevent attackers.
Kara offers a wide range of illuminated and non-illuminated Rocker Switches.Ranging from 1 to 6 poles,4VA to 30 amp,with many styles of colors and functions,especially the switches with High-Current used very widely in the welding machines. Certifications include UL, CSA, TUV, CE, and more. Kara Rocker Switches include the KR1-Series abd KR2- Series based on different size of the panel cut-out.

Rocker Switch,Waterproof Rocker Switch,Rocker Switch 3 Pin,Rocker Switch 4 Pin
Ningbo Kara Electronic Co.,Ltd. , https://www.kara-switch.com