The top hackers happy analytics: seven methods of human flesh search in baby events
As a man who dared to grab the headlines of the Olympic Games, Song Hao encountered a chase. This is not only the carnival of the entertainment industry, but also the science and technology circle has gone into confusion:
Without the participation of the majority of hacking enthusiasts, it seems that the paparazzi are unable to reveal Song Dai’s life experience, hobbies, address, and room records in a matter of days. It’s no exaggeration to describe it.
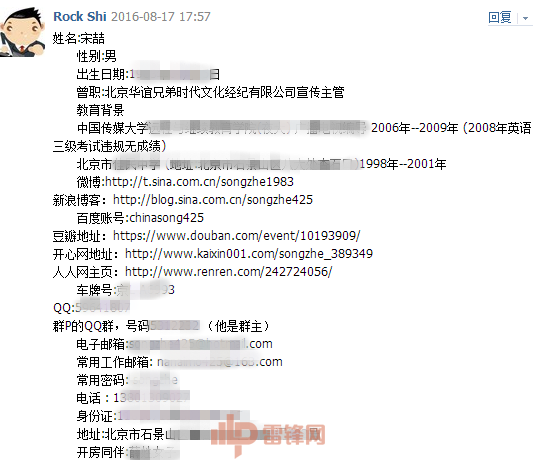

Song Yu’s personal information summarized by netizens (protecting the privacy of citizens, sensitive information has been coded)
In fact, hackers seriously captured the culprits and could get a lot of strange information that was surprisingly dropped. Lei Feng Network decided to consult with top hackers, temporarily put aside the legal and moral factors, what exactly is a human being? Or on the other hand, if you accidentally fall in love with the star's daughter-in-law and become a public enemy, how can you avoid being tragic with human flesh?
The Lei Feng network (search "Lei Feng Net" public concern) interviewed with security and professional hacker spirit security researcher - 360 network attack and defense laboratory boss Lin Wei . The following is dry goods.
First, the iPhone - a time bomb to carryTalk to you and pull out your iPhone. (if you have)
Open: Settings - Privacy - Location Services - System Services - Frequent Locations
When you see it, let me guess that the place where you go most is your home, and the second place is your company. If you feel that it is not detailed enough, click on the map. It is such a horror.
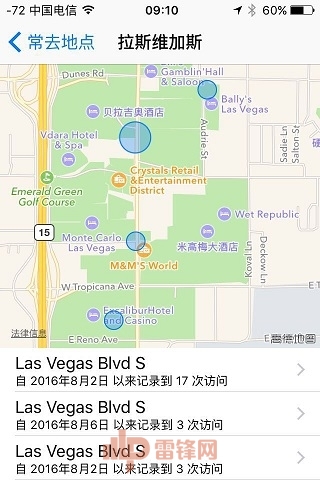
Apple's mobile phone will open the "frequently-located" function by default to completely record your life trajectory
If a hacker gets your iCloud account, log in with any iPhone to get your usual location information. So if you become a public enemy, don't be surprised that someone on the second day of the horse will block your way downstairs in your home.
Of course, things could not have been so complicated. Did you see "find my iPhone"?
However, all the information is based on the fact that your iCloud is cracked. The security of iCloud relies heavily on the strength of your password and the password strength of your secret email. If your secret email is NetEase, Oh.
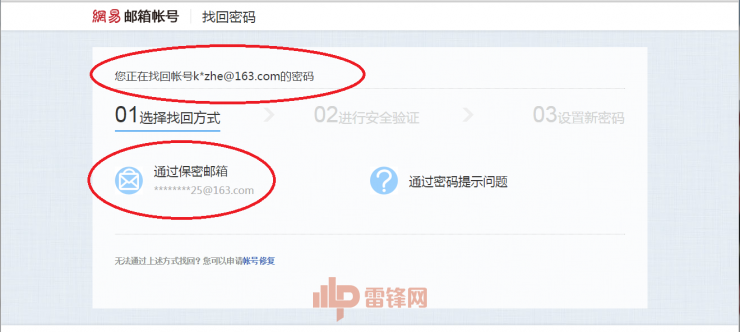
Song Wei's mailbox used the same weak password as the secret email used to retrieve the password. This allowed hackers to easily modify his email password.
This point is not ridiculous. Song Yong's commonly used mailbox is Netease, which is one of the key points he was a breakthrough. According to Ma Rong’s self-photographs circulating on the Internet, these images are likely to be Ma Rong or Song Yi’s iPhone. This means that it is very likely that hackers have captured at least one mobile phone.
Second, weak password - paper paste door lockThe situation in the real world is that within a few days Song Song's all mailboxes, Renren, and JD.com accounts seem to have been compromised. How do hackers do it? According to the information that broke out, Lin Wei simply sorted out the steps he was taken by the "social worker":
1. The mobile phone number and ID card information were leaked by users through the social worker library. (The identity card contained an address, but it later proved that the home was sold.)
2, NetEase mailbox password is cracked, implicated behind the secret mailbox and other common mailboxes.
3, using the mailbox to log in Renren, Douban account is to get.
4. JD.com, Volkswagen Review, and Takeaway App with the same or similar email password were compromised.
5. The exposure of an e-commerce merchant’s receiving address resulted in the removal of the hiding place and was blocked by the media.
We have traced the source, all of this has been cracked from the mailbox. As we all know, NetEase does not give power, once rumors have been dragged down (user database was hacked down). Although the official denies, multiple channels have proved that there is a complete user information of NetEase's mailbox in black production.
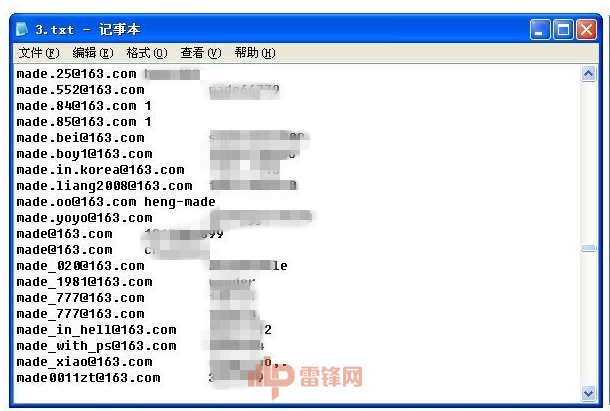
Netease mailbox password database circulating in black production
Because of this, you can see Song Yu's email password in the social worker library. However, there is one thing that must be explained, that is, the website is being dragged down. It does not mean that your password information will be leaked.
Popular science. Almost all user information on the site has now been "salted", that is, all user names and passwords are stored in an encrypted state. Even if hackers get into the website server and get your password information, they can't read the plaintext, but need to decode it through a password dictionary. The difficulty of deciphering is directly proportional to the complexity of the password. In other words, if your password is complex enough, it is still difficult to crack with the current computer's computing power.
In fact, the seemingly shrewd Song Hao is still less than an average person in terms of cyber security awareness. The simpleness of his password is appalling. To be exact, his common password is simply the pinyin of his own name, or adding his own birthday before and after. This caused a tragic encounter in which a series of accounts were cracked in a short period of time.
Then the question arises. How should we set the password to be safe?
Lin Wei told Lei Feng that the password should be the same as the movie, divided into at least three levels:
First level:
iCloud password, Wechat QQ password, Alipay password, you should set up more than ten digits, meaningless characters that are mixed with alphanumeric characters (If you like to memorize passwords with semantics, you can use a trick, that is, use 0 instead of o, use 1 instead i, etc.)
second level:
Jingdong, group purchase, take-out and other commonly used websites, set up more than eight, meaningless characters of alphanumeric characters. Note that the password cannot be partially overlapped with the first-level password. Otherwise, once the secondary password is deciphered, the secondary password can be used as a dictionary to easily decipher the first-level password.
Third level:
General websites, in order to take care of their IQ, can use relatively easy passwords that are easy to remember. The same attention must not be repeated with other two-level passwords, otherwise it is very easy to fall short.

Provide a few high-intensity passwords for children's shoes, forget to not blame me
3. WeChat Circle of Friends - Lurking + Infernal Affairs Do you know all your WeChat friends? I believe you will answer "no". So how do you determine if your friends circle is intimidating?
If you see old friends and friends who haven't been seen on WeChat for many years, look at the picture and you really know it. Will you pass the verification? Normal people will pass the verification in ten nine times.
However, the truth of the matter may be: the hackers get your old schoolmates' photos and basic information through your public information and friends information on the Internet, and then hide behind the WeChat to add you as a friend.
Once passed, your circle of friends is open to hackers. Think about it. Every photo you make in a circle of friends, every thought, can be a powerful proof that hackers can judge your position and character.
Lin Wei said:
Most people don't have high vigilance when sending content to friends. If you add a friend as a friend to a stranger and you seem to have high credibility, you'd better shield him from his circle of friends first, and then add friends. After that, first check the other person's circle of friends to make sure that the other person's identity is trusted. After that, let him open a circle of friends.
IV. Weibo, Renren, Watercress - Goodbye, PrivacyThe first thing that Song Hao had done after the incident was to clear his own Weibo. It seems that he also realized that the information he sent out on Weibo would become a "court proof" against himself. However, he did not empty his own Renren network at the first time. (The average person is really hard to realize at the first time that there is also the existence of artifacts in Renren.) This led hackers to get into his mailbox first and change the password of another person's network. It is very likely that he can no longer log in to his own Renren account.

It seems that the friends of Diba have occupied Song Ren’s Renren Network.
You may ask why Song Song cannot change the Renren password by logging in to the email? The answer is that, after his mailbox was exposed, there were already flooding netizens trying to log in all over the world and entered an abnormal state of protection. No one can already try to log in. In addition, even if there is no such human DDoS, as mentioned earlier, his email is likely to have been compromised and changed, so Song Song has lost control of his own mailbox.
Think about what you have done on everyone online? This social network, which is a bit overwhelming, lurks all your dark history. Take Song Song as an example. On Renren Online, you can openly search for his birthday, information about the school from childhood, he likes to keep dogs, his idol is Edison Chen, his character is not flustered and so on.
As we will mention later, when hacking other accounts or emails, these personal information will serve as answers to secret questions and play an important role in hacking.

Wang Haodan's two photos in the micro-blog led to the location of the user was targeted
Let's talk about Weibo, assuming that the human beings were not cleared the first time, and everyone can publicly view the information he has published. Because the issue of microblogging by human flesh, has been common:
Wang Haodan once published a picture taken from a window and was targeted by the netizen to her community, building number, and building number within a few hours based on the interior scene, window height, and lighting conditions.
Liu Qiangdong released photos of the same pot of tomatoes at the same time as her female assistant, and she was sulked by netizens.

Song Wei opened the microblog "Happy Life of Tabby Little DD" with the name of his own bulldog . The netizen used this photo to locate the area where he lived.
As a hacker with top security awareness hat, Lin Wei will also express emotions on Weibo and Renren, but he has some tips for publishing Weibo:
Try not to take photos that contain too much information. Try not to include location information. Try not to use the cryptic language that some people can understand, because if someone looks at you, the crypto is easily cracked.
Five, trumpet - secret clues pulled out secrets secretWhen people do bad things, they usually use trumpet.
In Song Song’s post about the girl, she revealed that it is not a commonly used NetEase mailbox, but a Hotmail mailbox.
Song Yun also understands this, so when the watercress is about “group Pâ€, it is not a common mailbox. In fact, Douban linked the relationship between his landing mailbox and the small mailbox.
When registering many trumpet, people will choose to use a separate mailbox, but many people often do not buy a new phone number to collect the verification code. Even if there are two mobile phone numbers, they will choose to live or work. one of. This will establish a connection between the virtual ID and the real identity.
Some people will have trumpet QQ, but in order to facilitate management, they often add friends and even pull groups. In this case, once the QQ password is compromised, it is easy to pull out your small QQ. If the size code uses the same password, it's easy to get a one-pot end.
Lin Wei said.
In fact, according to insider's news, Song Yong's commonly used mailboxes and small mailboxes used similar weak passwords, which led to the hackers directly rushed into Song Xiao's small mailbox and saw his dark side.
Song Xiao’s small mailbox was cracked by an anonymous hacker and provided a screenshot to Lei Fengnet. He was not allowed to watch under 18 years old.
However, the connection between trumpet and identity is far more than simple. Lin Wei cited some facts:
If you use the same device to log in to oversized WeChat and Small WeChat, then at WeChat's big data level, you will establish a relationship for both numbers.
If you use Baidu to search for some keywords anonymously, there will still be advertisements popping up on your device. These are all enforced in the service provider's big data.
In this case, the most secure trumpet use specification is probably as follows:
1, anonymously apply for a phone card
2. Apply for a temporary dynamic mailbox on a dedicated platform
3, use this temporary mailbox as a secret e-mail, apply for a new permanent e-mail
4, use a new dedicated mobile phone to log in trumpet, and not on any other device landing trumpet
5, two mobile phones can not be brought on the body at the same time, in order to prevent the location information overlap, associate; it is forbidden to open Wi-Fi, to prevent being fishing positioning.
Believe me, if Song Song used this small security gun of security level, few people around the world could find it.
Of course this "advanced trumpet guide" is just a joke. Lin Wei summarized: If you want to use trumpet to protect your privacy, it is necessary to achieve the separation of virtual identity and real identity as much as possible.
Six, takeaway, Jingdong, Taobao - sell your delivery addressThe public’s “encirclement and suppression†of Song Hao eventually turned the human flesh on the network into human beings in reality. The media finally intercepted Song Hao in accordance with various information. The key to meritorious service is likely to be e-commerce.
Lin Wei believes that these giant companies such as Taobao and WeChat have a high level of protection for user information and generally do not reveal any leakage. However, if the previously mentioned password grading is not done well, it will cause crashes (hackers crack the passwords of other platforms, and use these passwords to try to log in to Taobao and WeChat).
For example, platforms such as public comment, hungry, and Jingdong may have weaker security levels than BAT's "natural" platform.
In short, the leakage of e-commerce information will have a fatal effect, that is, your shipping address. The authenticity of these receiving addresses is very high, and it is very likely to include all the commonly used addresses of "people who are being fleshed" and relatives and friends.
Jingdong orders divulged in black production
Although entertainment reporters did not disclose, but Lin Wei inferred that the ultimate “informer†locates Song’s “hidden place†(actually the new apartment he purchased for his parents), probably because of the receipt of an e-commerce provider. Address leak caused. In addition, if the password of Song Song’s take-out software (such as Mei Da, hungry) has been controlled by hackers, once he has taken a place to hide, the meal address will immediately betrayed him.
Information leaked from e-commerce and take-away platforms is more than that. For example, there are hackers broke the news, Song Yu's Jingdong shopping records, there are a lot of dog food, so judge that he may go out in the morning and evening walking dogs.
7. Wi-Fi - The Eye of GodYou may not believe that as long as your mobile phone has always been turned on Wi-Fi, in theory, hackers can use a method to track your space trajectory.
First to be a science:
All mobile phones will broadcast the Wi-Fi name they once connected to as long as Wi-Fi is turned on. As long as there is a Wi-Fi with the same name in the signal range, the phone will automatically try to connect.
This is an amazing act that Lin Wei is incomprehensible.
Lin Wei imagined such an attack pattern:
First of all, at the door of the Song Dynasty, Wi-Fi signals were searched with random devices. The strongest signal was the Wi-Fi in the Song Dynasty's home and Mark's Wi-Fi name.
Then use a Wi-Fi signal transmitter called "big pineapple" to send out the Wi-Fi signal with the same name as Song.
Finally, put the "big pineapple" in the place where Song Song may pass. Once a mobile phone is connected to the Wi-Fi signal, the "big pineapple" will return a signal to the controller.

Big Pineapple Wireless Signal Transmitter (Pineapple Wireless)
This "big pineapple" can have many (if you have enough funds for the rape), arranged in the doorway of the residential garage, the doorway of the corridor, and all the places where he may settle. In this way, it is as if the camera is full of cameras in the city. As long as the signal is received, it means that the tracked person (or close family member) has passed through the site. (You can determine the specific identity of the connection by connecting the device's name.)
"Big Pineapple" can not only provide fake Wi-Fi signals but also provide true Wi-Fi functionality. However, plaintext messages transmitted on these "fishing Wi-Fi" can be viewed by attackers.
Because this kind of attack method is based on the exotic protocol of Wi-Fi, Lin Wei also said that there is no good defense method. "Opening Wi-Fi only when necessary is a helpless method."
What else is there?The above describes many ways to “escape†in Beijing City. However, the “public enemies†that encounter human flesh and social workers may fly abroad for the first time. How to judge whether a person "escaped"?
"Have you heard of air travel?" Lin Wei asked.
Air Travel
Many of the children's shoes that often fly are used by Air Travel. It can present all of a person's flight information. In past versions, you only entered your ID number and you can check your own voyage. Similarly, if you enter someone’s ID number, you can also check the other’s voyage.
Lin Wei told Lei Fengwang that in the new version of Air Travel, App’s identity verification for queriers has become more stringent, requiring users to upload their own ID photos.
He said:
In this case, the attack is more troublesome. Because you need an ID for PS.
That's right, it's hard for auditors to tell the authenticity of an identity card.
"Another bank card with flash payment function also has a wonderful feature." Lin Wei added, "If you read it with an NFC device, you will get the latest ten consumer records. This attack only requires the use of equipment on each other." It would be nice to scan around, and when those entertainment records were enshrined in the Song Dynasty, they should not only be interviewed, but they should also scan him with such equipment."
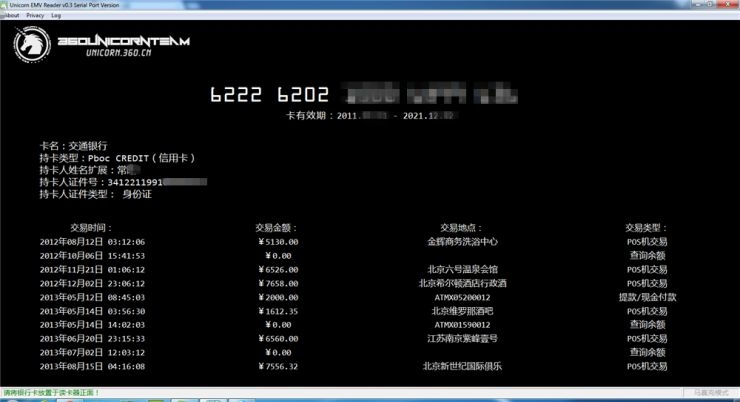
Use a specific NFC device to scan the card, card number, cardholder's name and ID number, and the last ten transaction records can be read/photo courtesy of the 360 ​​Unicorn team
Lin Wei said that as a hacker, stress the heart. If you just want to find Song Song, then the above skills are more than enough. However, what people want more is the truth. The premise of obtaining the truth is that Song Yu and Ma Rong had a crack.
In Lin Wei’s view, the Song’s open house record circulating on the Internet is one of the types of attack. Objectively speaking, only the police can master the details of the open house records of the clock room. Therefore, the source of this information seems to never have an answer, and the police naturally will not come forward to clarify. As a result, no one can ever prove the authenticity of this record. Looking further, supposing this open house record is hacked by the hackers, then to a certain extent, the result of aggravating the mutual suspicion of the two people is achieved.
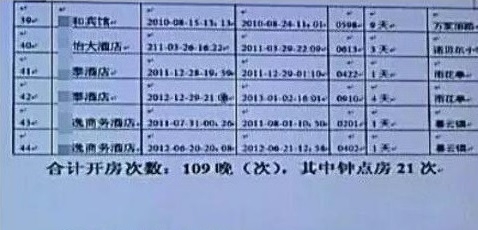
Net exposure Song Yu open house records
Suddenly awake. The highest realm of hackers was to place a time bomb in the spiritual world.
It is time to spread positive energy. As a senior hacker, Lin Wei knows the boundaries of law and morality.
It is illegal to use a social worker method to invade the account of another person. It is also an immoral act for others to be human. The reason why these attack methods are introduced is because everyone in the Internet era faces the threat of attacks. Knowing how to attack can be more effective defense.
He said.
From this point of view, the history of Song and tears taught us at least two things:
Look at your own wife and don't move other people's wives;
Be optimistic about your password, don't move anyone else's password.