WLAN standards, security and roaming
At the beginning, many emerging wireless broadband technologies will advertise that they will become mainstream technologies in the future, such as WLAN (Wireless Local Area Network), Bluetooth, HomeRF, UWB (Ultra Broadband), etc., but they can really stand the test of the market and obtain most People who agree, I am afraid that only the IEEE 802.11 series of WLAN is enough. From the application point of view, WLAN has been proposed for many years, but because it has always been positioned solely as an extension of wired LAN, coupled with the lack of a unified standard and low transmission rate, it is not used much and is difficult to promote. Until the end of the last century, with the advancement of WLAN technology and the unification of standards, it has been widely used as a high-speed wireless access technology for the Internet. It has been widely used in offices, airports, hotels, shopping malls, coffee houses and other public institutions. Hot spots (hotsports). Therefore, it was rated as one of the top ten trends in US communications technology in 2000.
Changes in WLAN standards
The IEEE 802.11 series of standards includes several new standards such as 802.11a, 11b, and 11g, which were introduced in succession in addition to 802.11 announced in 1997. From a technical point of view, 802.11a occupies the 5GHz free frequency band. Because there are not many other applications in this band, there is less interference; it uses orthogonal frequency division multiplexing (OFDM) technology with a higher transmission rate, within 10m Its rate can be as high as 54Mb / s, but as the distance increases, its rate drops rapidly, and it will drop to less than 10Mb / s at more than 70 meters. 802.11b occupies a free frequency band of 2.4GHz, but because many countries use cordless phones, Bluetooth devices and even microwave ovens, the interference is greater. It uses relatively simple direct sequence spread spectrum (DSSS) technology, and its rate can theoretically be It reaches 11Mb / s, but considering the overhead of the physical layer (at least about 40%) and the free frequency band is susceptible to interference, the rate is much lower than this. Although 802.11a began to be formulated earlier than 802.11b, but because 802.11b is easy to implement and completed earlier, 802.11b products have occupied a larger market share.
Obviously, due to the use of different frequency bands, 802.11a products are not compatible with 802.11b. To solve this problem, IEEE developed the 802.11g protocol, which improves speed and transmission distance on the basis of compatibility with 802.11b. There are two modulation methods specified in 802.11g, including OFDM used in 802.11a and CCK (complementary code keying modulation) used in 802.11b. By specifying two modulation methods, it not only achieves the data transmission speed of 802.11a level in the 2.4GHz band, but also ensures compatibility with 802.11b products with more than 11 million installed units. TI's proposed PBCC-22 (CCK-PBCC) modulation method and CCK-OFDM, which can achieve 22Mb / s data transmission speed, can also be used as options. Therefore, 802.11g is actually a hybrid standard. It can adapt to the traditional 802.11b standard and provide 11Mb / s data transmission rate per second at 2.4GHz frequency, and also comply with the 802.11a standard to provide 54Mb / s data transmission at 5GHz frequency. rate. However, the cause of interference determines that 802.11g cannot reach the high rate of 802.11a, and this protocol was only formally approved in July 2003, which has caused many equipment manufacturers to switch to 802.11a directly.
Although the highest rate of the 802.11g standard can also reach 54Mb / s, for multimedia services to be developed in WLAN in the future, this rate is far from enough. Therefore, IEEE has established a new working group to prepare a new high-speed WLAN standard 802.11n. The standard uses multiple input multiple output (MIMO) technology and OFDM technology, plans to increase the transmission rate of WLAN from 54Mb / s to more than 108Mb / s, in order to achieve seamless integration with 100M wired network, the highest data rate is expected to be Up to 320Mb / s.
WLAN In addition to some of the main standards mentioned above, IEEE is constantly improving these protocols. New protocols that are introduced or are about to be launched include: 802.11b version 802.11d that does not use the 2.4GHz band, improves the QoS (quality of service) of the 802.11 protocol 802.11e, 802.11f with improved switching mechanism, 802.11i with improved security mechanism, etc.
Once the transmission technology standard is determined, the research focus of WLAN should be transferred from the development of hardware products to software accordingly to solve some of the problems it currently encounters: first, security problems, all networks have security problems, However, the wireless network has its own particularity; the second is roaming, which is different from the roaming problem of mobile networks. The roaming problem of WLAN is more a problem of roaming between different operators, as well as billing and billing problems.
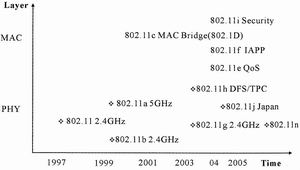
Figure 1 802.11 related standards development blueprint
Figure 2 Wi-Fi and Bluetooth application schematic
Security issues In any network, data security issues should be the focus of consideration, but security is the weakest part of WLAN. As a relatively reliable wired network security solution, VPN (Virtual Private Network) technology has been adopted to a certain extent in enterprise wired network applications. However, in a wireless network, due to factors such as sudden interference or handover between APs (access points), wireless link quality fluctuations or short-term interruptions may cause short-term interruption of user communication links. Once the link is interrupted, users will have to manually set up to restore the VPN connection. This is unbearable for WLAN users, especially those who need mobile or QoS guarantees (such as VoIP services). In addition, the higher complexity and cost of VPN networks also largely hinder the application of VPN technology in WLAN. As early as October 2000, WEP (Wired Equivalent Privacy), a standard security protocol based on the RC4 algorithm adopted by 802.11b, was found to have a security vulnerability. It uses a 24-bit initial vector and a 40-bit key to encrypt data, and each user uses the same key, which means that a user's security vulnerability will threaten the security of the entire network. Some new products now support WEP2 (later IEEE named it TKIP: Temporal Key Integrity Protocol, Temporal Key Integrity Protocol). Although it uses a 48-bit initial vector and a 128-bit key, it still does not leave WEP2 The core is fully compatible with WEP. However, the security vulnerability of the WEP algorithm is caused by the WEP mechanism itself, and has nothing to do with the length of the key, so increasing the key length is impossible to enhance its security, and the increase in the initial vector length can only increase the difficulty of cracking to a certain extent. , Prolong the cracking time, and can not fundamentally solve the problem. To some extent TKIP is more vulnerable because it uses Kerberos passwords, which can often be broken with simple guessing methods. The Wi-Fi Alliance and the IEEE 802 committee also acknowledged that TKIP can only be used as a temporary transition plan, not a final plan. In the long run, AES (Advanced EncrypTIon Standard) encryption method is used.
In addition to improving security by encrypting the data to be transmitted, WLAN can also enhance its own security by strengthening user authentication. The original 802.11b used a service group identifier (SSID), but because it uses a broadcast format, users can receive it, so it is easy to be cracked. WLAN later adopted the IEEE 802.1x authentication method, but 802.1x was not specifically designed for WLAN, it did not take into account the characteristics of wireless applications. 802.1x provides authentication between the wireless client and the RADIUS server, not between the client and the wireless access point AP; user authentication with a user name and password is used, so it is still in storage, use, and authentication information transfer There are great security risks, such as leakage and loss.
Therefore, the security solution given by the IEEE 802.11i standard currently under development is: CCMP (CBC-MAC Protocol) encryption technology based on 802.1x authentication, that is, using AES as the core algorithm, using CBC-MAC encryption mode, with packet The initial vector of the sequence number. CCMP is a 128-bit block encryption algorithm, which is more secure than all the aforementioned algorithms.
Of course, before the new standard is officially promulgated, some simple security remedies that can be adopted are: pay attention to key management when using the WEP protocol, replace the default key daily or weekly; protect the hard disk and files with a password Folder; change the default SSID; use the session key provided in some products; use the MAC address filtering function provided in some products, etc.
Our national standard GB15629.11-2003 uses a security protocol called "WLAN Authentication and Privacy Infrastructure" (WAPI), not the WEP or TKIP security protocol used in the 802.11 standard. Technically, the WAPI security mechanism is different from current international standards. WAPI uses the public key system's elliptic curve cryptographic algorithm and secret key system's block cipher algorithm approved by the Office of the National Password Management Committee, which are used for digital certificate of WLAN equipment, key negotiation, and encryption / decryption of transmitted data, respectively. The device's identity authentication, link verification, access control and user information encryption protection in the wireless transmission state. It has been reviewed and approved by the IEEE RegistraTIon Authority authorized by ISO / IEC, and has been assigned the Ethernet type field for the WAPI protocol. This is also the only agreement currently approved in this field in China and is awaiting submission to the ISO / IEC JTC1 committee.
From a market perspective, WAPI fully considers market applications. The application mode is divided into two types: single-point and centralized: single-point is mainly used for small-scale applications of homes and small companies; centralized is mainly used in hot spots and large enterprises, which can be combined with the operator's management system, Work together to build a secure wireless application platform. Users can safely apply WLAN in homes, companies, hotspots and other regions without worrying about security and interconnection between devices.
The roaming problem and the integration of 3G with different WLAN coverage distances are also different. Most 802.11b networks can transmit a distance of 100 meters. Using a higher power transmitter can extend the coverage distance, but at the same time, the signal will be more interfered and the obstacles encountered will be more. In addition, considering the security, WLAN requires to limit the transmission power, which affects the transmission distance. The transmission distance of 802.11a is similar to that of 802.11b. Although in principle high-frequency electromagnetic waves are easier to be absorbed and the transmission distance is shorter, because 11a adopts OFDM technology, it can overcome the influence of multipath effect. Taking these two factors into consideration, it is easy to conclude that their coverage distance is not much different in conclusion. However, it should be noted that the 54Mb / s rate of 802.11a is achievable within 10 meters. As the distance increases, the rate decreases quickly, and it drops to within 10Mb / s at more than 70 meters.
Since 802.11g is a new standard, there is no experimental data to explain its transmission distance, but it is speculated from the principle of OFDM technology that it should be able to reach a farther distance. Of course, increasing the transmission distance is not entirely an advantage, because wireless bandwidth is shared, and increasing the distance means that the number of users increases, and the bandwidth that can be allocated by each user decreases accordingly. Therefore, 802.11g is suitable for environments where there are few users or where users have low bandwidth requirements. Another problem is that signals will leak over long distances, and intruders may break into the network from the far end. To solve this problem, a directional antenna can be used.
In summary, due to the limited power of WLAN, its service coverage area is limited, and its convenience is greatly reduced. However, if we try to connect the various WLANs together, we can form a wireless metropolitan area network, allowing portable Internet devices such as notebook computers and PDAs to move wirelessly in the same city to meet the access requirements in the mobile state. In the wireless network IP planning, it is assumed that the "floor" is defined as a network segment, and users in the building can only maintain fixed IP movement on their own floors, or switch between network segments between different APs. If the user leaves their own floor to the business activity area downstairs, they have to modify the original IP address in the computer or use DHCP to regain a temporary IP to surf the Internet. However, at this time, the user can no longer return to his office network to obtain the corresponding network data and normal network working ability.
With the help of mobile IP technology, that is, multiple areas on the IP network can use the same IP address, through the use of special routers called HomeAgent and ForeignAgent, the network where the network terminal is located is carried out. Management can realize roaming between different network segments of WLAN. From the operator's perspective, this is the problem of roaming between networks. If roaming is not possible, consumers need to purchase networks from multiple operators. When accessing networks of different operators, laptops need to log in again, and people do not know how to identify who is the operator in a specific area? Therefore, consideration should be given to enabling multiple wireless ISPs to share the statistical information and billing information of users' use of the network, to coordinate the distribution of benefits among wireless ISPs, and to achieve interconnection between different operators.
However, when roaming can be realized, it is still difficult to say. But it is gratifying that the world ’s largest wireless broadband operator alliance (WBA) announced at the third meeting in July 2003 that Wi-Fi international roaming will be in China (Netcom), Australia, Malaysia and Singapore. The country conducted a pilot test, which proposed a global brand identity, a standard login interface and Wi-Fi international roaming, designed to ensure that wireless broadband services can continue to operate stably in different countries, and the network can be smoothly and seamlessly connected, thereby ensuring users more convenient To achieve wireless Internet access.
Although the access rate of WLAN is very high, neither local area network nor metropolitan area network can obtain data in fast movement. Currently, only cellular networks, namely 2G and 3G, can be accessed in a fast moving environment. Because this type of network covers a large area, it can also be called a wireless wide area network. But the shortcoming of the United States and China is that its data transmission rate is very low. Even under ideal conditions, the data transmission rate of 3G can only reach 2Mb / s, which is far from the 11Mb / s of 802.11b. Therefore, it can only achieve "unlimited coverage, limited bandwidth"; in contrast, WLAN extended from a wired LAN has the characteristics of "limited coverage, unlimited bandwidth". Therefore, in places where new lines cannot be deployed, WLAN can be used as a supplement to wired LAN; in some "hot spots", WLAN can be used as a 3G competition solution. From this perspective, WLAN and 3G are not perfect. Different technologies and different solutions are positioned on the market differently. There may be a relationship of substitution, but it is more likely to be a symbiotic relationship. For example, China Mobile has associated with Lenovo to connect a GPRS module to a laptop network card and use the SIM card to access the Internet and billing. It is trying to find the most suitable space in the confrontation between wireless WAN and WLAN. But in any case, WLAN will definitely have a big impact on 3G.
China's WLAN strategy The National Standardization Management Committee has officially issued the China WLAN GB 15629.11-2003 series of standards drafted by the "China Broadband Wireless IP Standards Working Group" (). The WLAN standard is based on the principle of adopting the international standard ISO / IEC8802.11 series of standards, and on the basis of fully considering and taking into account the interconnection and interworking of WLAN products, technical solutions and specification requirements are given for WLAN security issues. It incorporates the country's requirements for cryptographic algorithms and radio frequencies. It is based on the WLAN standard that complies with China's safety standards based on international standards. These two standards are nationally enforced standards and will be officially implemented in June 2004. At that time, WLAN products that do not meet this standard will not be allowed to appear on the market.
Although the promulgation and enforcement of our national WLAN standards have caused great impact, this is the concrete implementation of China's information security strategy, which shows that our country has taken a solid step forward.
UCOAX Custom Made Link Cable Compatible for Oculus Quest 2, Fast Charging & PC Data Transfer USB C 3.2 Gen1 Cable for VR Headset and Gaming PC 16FT(5M)
Compatible for Oculus Quest 2: KRX link cable has perfect compatibility for oculus quest 2, so you can enjoy your gaming time happily
Flexiable lengths of link cables for you to choose. Choose the right one according to your needs
High-speed transmission & Fast Charging: The 3A current allows you to charge quickly while playing, maintaining stable and high-speed data transmission
USB C cable version: KRX USB C cable compatible with usb 3.0/3.1 gen1/3.2 gen1
90 Degree angle metal head design: The 90-degree USB C design makes you more stable and not easily damaged when playing
Virtual Reality Link Cable,Oculus 2 Cable,Vr To Pc Cable,Virtual Reality Link Cable Device
UCOAX , https://www.ucoax.com